Web Applications, Infrastructure and Security training
This Web Applications, Infrastructure and Security training offers a unique overall view of Web Applications, Infrastructure, Architecture and Security, in stead of attending multiple product specific courses. It explains the dependencies and relationships between the different components and you will learn the essentials of each component.
This training is available as a classroom training as well as a webinar: live connected to the instructor using Skype or Zoom.
This Web Applications, Infrastructure and Security training is meant for:
- for DevOps engineers who need more knowledge of infrastructure (hybrid cloud), design and security and be prepared for the “shift left”.
- For Infrastructure specialists who need more knowledge of software development, for example client-side development/Javascript, Java or continuous integration.
- For Managers and Product Owners who need more technical knowledge.
This Web Applications, Infrastructure and Security training (6 sessions of 4 hours) offers the essential knowledge to understand the complete application chain. It provides insight in Web Applications and the necessary infrastructure. You will learn important architectural principles as security (including High Availability) and SOA (REST API’s, microservices, loosely coupled etc. etc.)
This Web Applications, Infrastructure and Security course is suitable for everybody closely involved in IT: Product Owners, Customer journey experts, management and IT staff. Furthermore, there will be a higher demand for IT generalists when moving to the cloud: this course is a perfect preparation for IT engineers to migrate to the cloud.
The Cloud (self service portals) causes a shift in responsibilities: DevOps must have infrastructure and security knowledge (DevOps must own the stack, DevSecOps) and cannot fall back on an IT infrastructure department.
This Web Applications, Infrastructure and Security training answers the following questions:
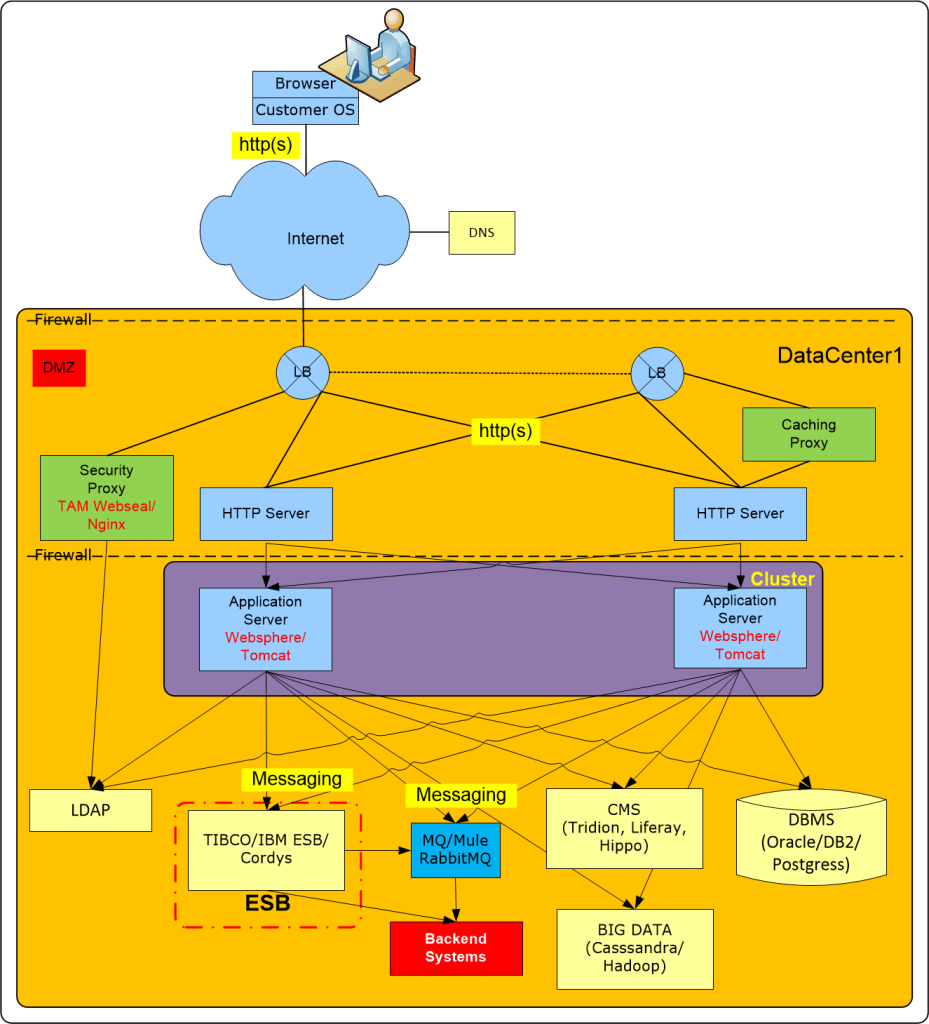
- How does a Load Balancer work, a firewall, a secure reverse proxy, DNS, etc. etc.? What’s a DMZ?
- How can I achieve High Availability and how do I prevent losing data?
- How does Disaster Recovery (DR) work? Why do we prefer active-active?
- What are the consequences of migrating to the cloud and how can I avoid a vendor lock in?
- What is a cloud native application?
- What are the advantages of client-side development (javascript, Polymer, etc.)
- What is a webservice (REST API’s, microservices) and loosely coupled?
- How do I manage my application chain?
- What are the consequences of using containers (Docker) and immutable servers?
- What are the advantages of an event-driven architecture?
- How do I secure my data and applications?
- What is the importance of network segmentation?
You will learn the ins and outs of the most important middleware products and the latest trends in application development, architecture and security will be discussed.
The focus is on Changeability (integration and scalability) and Security (including high availability, disaster recovery and operational management). Complex subjects are explained using examples and case histories.
After attending this Web Applications, Infrastructure and Security training, you will have in-depth knowledge of all components part of an application chain. You will be able to apply best practices in IT architecture and security.
You can find a detailed agenda at the end of this page.
After attending this training you will receive the slides in PDF format as well as the application design best practices.
This training can be enriched with Enterprise Specific information, see our way of work.
Web Applications, Infrastructure and Security training overview
The training is divided in six modules of 4 hours:
- Web Applications and IT Infrastructure essentials
- Apply application integration essentials
- Java Application Servers, Open Source and Big Data solutions
- High availability (including disaster recovery) and Operational management (application chains)
- Virtualization, Cloud Computing & Application Containers
- IT Security and network essentials
Course Duration classroom/Webinar-remote/online
The Web Applications, Infrastructure and Security training can be delivered in 6 morning/afternoon sessions or 3 days. Repetition and retrospection will ensure the students will learn and retain the information acquired.
Price
The Web Infra Academy uses two price models: per student or per training. For more information or a quotation please contact us or use the form at the end of this page.
Our courses are also offered by our global partner Global Knowledge.
- Classroom: 1995,00 Euro per student
- Webinar – Remote/online: 1495.00 Euro per student (met Skype of Zoom)
- E-learning: under development
- Blended: under development
Course dates Web Applications, Infrastructure and Security classroom training
Startdate 12-04-2023 – end date 03-05-2023, Webinar or classroom, Nieuwegein
- Part 1: 12-04-2023, from 09:00 to 13:00
- Part 2: 14-02-2023, from 09:00 to 13:00
- Part 3: 19-03-2023, from 09:00 to 13:00
- Part 4: 21-03-2023, from 09:00 to 13:00
- Part 5: 26-03-2023, from 09:00 to 13:00
- Part 6: 03-05-2023, from 09:00 to 13:00
Please register using the form at the end of this page.
This Web Applications, Infrastructure and Security training is also available through our partner Global Knowledge, code training GKTIWIB.
Prerequisites
- Basic browser experience
- Basic IT knowledge
Target audience
- Product Owners
- Customer journey experts
- DevOps and IT Engineers
- Management
- Enterprise Architects
- Starting IT-specialists
- IT staff
Skills acquired
Module 1: Web Applications and IT Infrastructure essentials
- Explain how a web application works (http, cookies, session affinity etc.)
- Identify the middleware components part of the application chain:
- Firewall
- Load Balancer
- DNS
- DMZ
- http server
- Secure Reverse proxy (NGINX etc.)
- Understand the TCP/IP transport protocol and the BGP protocol
- Understand the HTTP protocol and explain session management (stateless and stateful).
- Explain the security controls offered by SSL/TLS and identify the steps for a successful SSL/TLS handshake
- Understand the difference between symmetric and asymmetric encryption
- Understand why certificate management is vital
Module 2: Application integration essentials
- Identify the differences between Java and Dotnet
- Explain the popularity of client side development (Javascript, Angular, Polymer etc.)
- Explain the difference between synchronous and asynchronous processing
- Understand the principles of messaging and the differences with the HTTP protocol
- Understand de advantages and disadvantages of the Request-Reply model versus Fire-Forget
- Explain the difference between point-to-point and publish-subscribe
- Understand the impact of persistent messaging and non-persistent messaging
- Identify the popular messaging products (Kafka, RabbitMQ, websphere MQ, Fuse, etc.)
- Explain the principles of SOA
- Identify the functions of an Enterprise Service Bus
- Understand the advantages of a webservice
- Identify the differences between SOAP, REST (Web API’s) and Microservices
- Understand why governance is of utmost importance in SOA
Module 3: Java Application Servers, Open Source and Big Data solutions
- Explain the advantages of a container architecture
- Identify the most important functions of a Java Application Server
- Explain Java Class Loading
- Understand the impact of Garbage Collection
- Identify a Memory Leak
- Identify the tuning parameters of a Java Application Server
- Understand the differences between Tomcat, IBM WebSphere, JBoss, etc.
- Understand the implications of standalone executables (Scala-Akka, Kotlin)
- Explain the popularity of Open Source products
- Open Source versus Managed Service (or cloud)
- Identify the popular Open Source products:
- Apache Kafka eventbus, PostgreSQL, MariaDB, SQLite
- Logstash, Nagios, Elasticsearch, Tomcat, Docker, Kubernetes
- Identify the characteristics of NOSQL-databases
- Understand the advantages of Big Data solutions (Cassandra, Hadoop etc.)
Module 4: High Availability, Operational Management and Application Chains
- Understand the different levels of high availability (DR versus component failover, Active-Active versus Active-Standby)
- Explain why and when latency can be an issue
- Explain the terms Recovery Time Objective (RTO) and Recovery Point Objective (RPO)
- Compare the advantages of horizontal and vertical scaling
- Explain the importance of testing the non-happy flow:
- Understand the problems with (automatic) failover mechanisms
- Understand the advantages of an event-based architecture versus Request-Reply
- Understand the problems with (long) application chains
- Understand data(-base) resilience and data replication techniques
- Understand the difference between synchronous and asynchronous data replication
- Explain how to ensure data integrity and consistency
- Identify the necessary tools for operational management
- Monitoring tools (IaaS/PaaS/SaaS level, active-passive)
- Central event Collector
- Log collectors (Logstash/Splunk), central log servers and log analyzers
- Service management and configuration management tools (CMDB, uCMDB)
- Describe automated failure testing: Failure as a Service (FaaS – Simian Army – Chaos Monkey),
- Explain the principles of Self-Healing
Module 5: Virtualization, Cloud Computing & Application Containers
- Identify the advantages of Virtualization
- Describe the characteristics of VMWare (VMotion)/Hyper-V
- Explain how virtualization enables the Cloud
- Cloud Essentials (characteristics, deployment models)
- Explain the shift in responsibilities
- From Infra management to development of services/API gateways for integration and orchestration
- From Infra Engineer to DevOps and vice versa (IT generalist)
- Cost awareness, security awareness (DevSecOps)
- Explain the importance of API-gateways (Cloud integration using API’s)
- What is Policy-based-automation and which tools are available?
- Understand the advantages of Elasticity/Autoscaling
- Explain the term Serverless computing
- What is a Cloud Native application?
- Understand the difference between Virtualization and Application Containers (Docker, OpenShift Kubernetes)
- Identify the advantages of Application Containers
- Understand the 12-factor App principles
- Explain the main components of Docker
- Understand the terms Pets, Cattle and Ants
- Explain the advantages and prerequisites of immutable and inaccessible servers
- Understand why adaptive is the buzzword in IT
- Explain the popularity of Machine Learning
Module 6: Security and network essentials
- Understand the IT security criteria: Confidentiality, Integrity and Availability
- Explain why IT-security is vital, especially now (APT, etc.)
- Understand the importance of data qualification and risk assessment
- Explain “Defence in depth” and “layered defence“
- Identify the most important controls of all IT layers
- Explain RBAC
- Describe the most important security tools (Security Event Monitoring – SEM and Machine State Monitoring – MSM, etc.)
- Understand the advantages and disadvantages of networksegmentation and the network perimeter model
- Understand how a firewall works and what a WAF (application aware firewall) is
- Understand the principles of a Zero trust network (continuous authentication, mutual TLS)
- Understand the necessity of Single Sign On (SSO)
- Explain the functions of a security Gateway (NGINX/etc.)
- Understand the usage of NATting
- Understand the necessity of IPV6
- Explain the impact of IoT
If you have any questions or are interested in this Web Applications, Infrastructure and Security training, please contact us or use the form below:


